The concept was first introduced by John Kindervag of Forrester Research, who noted that “trust is a vulnerability, it’s something attackers exploit.” Today, Zero Trust is no longer a theoretical model—it is a practical requirement for enterprises, SMBs, and government organizations worldwide.
🔐 Core Principles of Zero Trust
Zero Trust is built on three fundamental principles that shape every implementation:
- Verify Explicitly: Always authenticate and authorize based on all available context—user identity, location, device health, role, and workload.
- Use Least Privilege Access: Grant only the minimum permissions necessary for users or applications to perform their tasks.
- Assume Breach: Operate under the assumption that attackers are already inside the environment and design systems to minimize damage.

🚨 Why Zero Trust Matters in 2025
Traditional security models relied heavily on firewalls and VPNs to protect an internal network perimeter. However, remote work, hybrid IT, SaaS applications, and cloud adoption have rendered perimeter-based defenses obsolete. Attackers now exploit identity, access, and misconfigurations instead of breaking through firewalls.
According to the IBM 2024 Cost of a Data Breach Report, the global average breach cost has climbed to $4.88 million. By enforcing granular identity controls and continuous monitoring, Zero Trust reduces these risks significantly.
Key use cases where Zero Trust is essential:
- Remote & Hybrid Workforces: Employees securely access apps from any location or device.
- Cloud Environments: Protect workloads and sensitive data across Azure, AWS, and Google Cloud.
- IoT & OT Devices: Segment and isolate vulnerable devices like smart cameras or industrial controllers.
🧱 Key Components of Zero Trust Architecture
1. Identity and Access Management (IAM)
IAM is the foundation of Zero Trust. Tools like Microsoft Entra ID (formerly Azure AD) and Okta enable centralized authentication, conditional access, and single sign-on (SSO).
2. Multi-Factor Authentication (MFA)
MFA strengthens security by requiring two or more verification factors (e.g., password + fingerprint). Microsoft research shows MFA blocks 99.9% of automated attacks.
3. Micro-Segmentation
Networks are divided into smaller zones so that even if one is breached, attackers cannot move laterally.
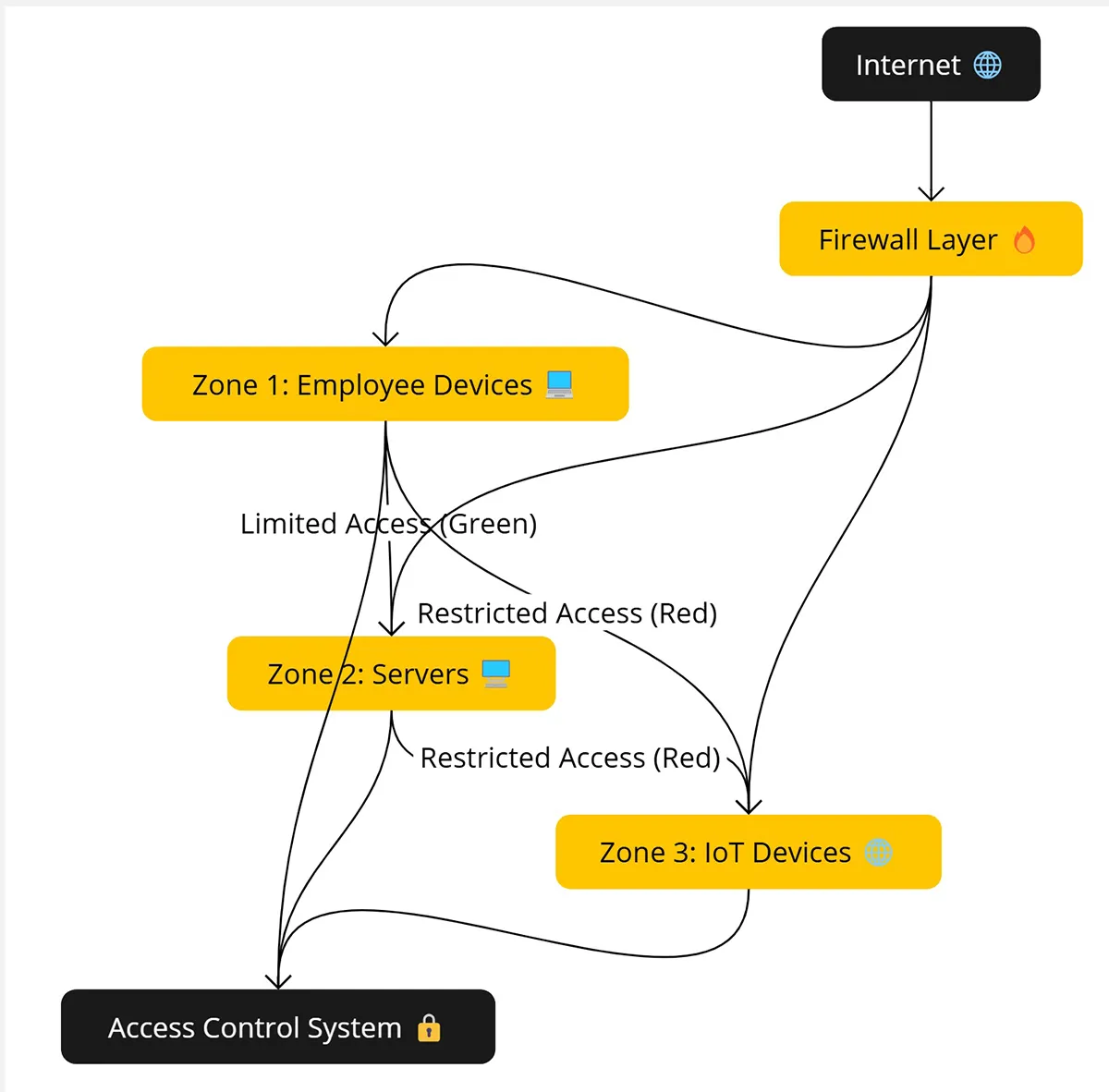
4. Endpoint Security
Endpoints such as laptops, phones, and tablets are constantly monitored. Platforms like CrowdStrike and SentinelOne deliver real-time protection and remediation.
5. Continuous Monitoring & Analytics
Tools like Splunk and Palo Alto Cortex XDR provide behavioral analytics, alerting administrators to unusual patterns before damage occurs.
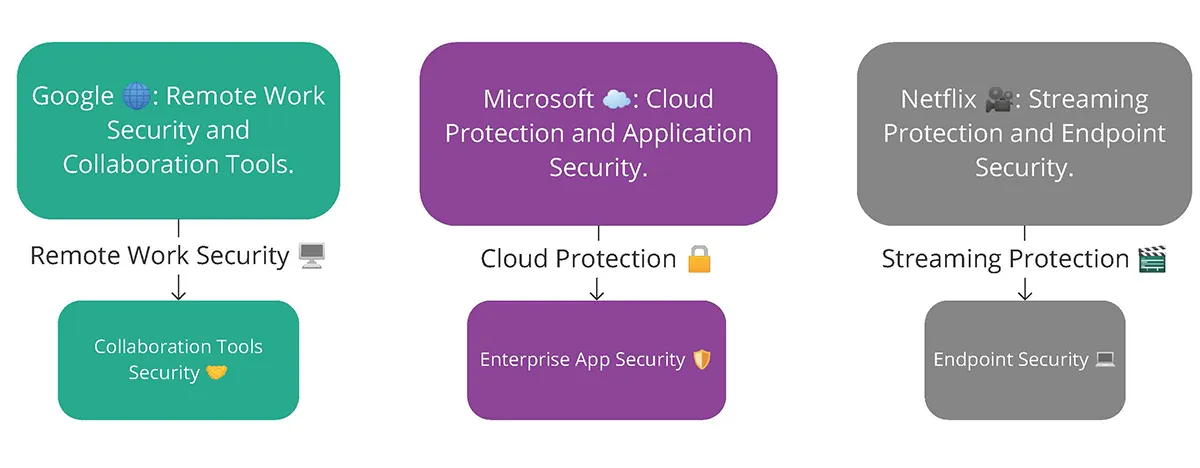
💼 Real-World Examples of Zero Trust in Action
- Google BeyondCorp: Allows employees to securely access resources without VPNs.
- Microsoft: Applies Zero Trust across its Azure, Office 365, and enterprise infrastructure.
- Netflix: Uses Zero Trust to protect internal production workflows and customer data.
🛠️ How to Implement Zero Trust Security
Zero Trust is a strategy and journey, not a one-time product. A phased approach is recommended:
- Assess Current State: Identify all users, devices, applications, and data flows.
- Enforce Identity & MFA: Deploy IAM with MFA as the first baseline step.
- Implement Micro-Segmentation: Use VLANs, firewalls, or SDN for network segmentation.
- Secure Endpoints: Roll out EDR solutions across all endpoints.
- Enable Continuous Monitoring: Use AI/ML tools for behavioral analysis and anomaly detection.
⚠️ Challenges and Considerations
- Complexity: Migrating from legacy systems requires careful planning.
- Cost: Licensing and configuring IAM, MFA, and monitoring tools may be resource-intensive.
- User Experience: Too many security prompts may cause “alert fatigue” if not optimized.
Pro Tip: Start with a small pilot project (e.g., finance department or HR apps) before scaling organization-wide.
🔮 Future of Zero Trust Security
- AI Integration: AI and machine learning will drive automated anomaly detection and faster incident response.
- Automation: Automated policy enforcement will reduce human error.
- SMB Adoption: Cloud-native toolkits are making Zero Trust feasible for small and mid-sized businesses.
Related Articles
- Protecting Your Personal Computer from Remote Access Trojans
- AI in IT Operations: Use Cases and Benefits
- Cybersecurity Incidents: Real-World Lessons to Safeguard Your Business
Frequently Asked Questions
What is the main goal of Zero Trust Security?
The main goal is to eliminate implicit trust and continuously validate every access request, regardless of source.
Is Zero Trust a product or a strategy?
Zero Trust is a strategy. It combines IAM, MFA, micro-segmentation, endpoint protection, and continuous monitoring.
How long does it take to implement Zero Trust?
Implementation timelines vary. Most organizations begin with IAM + MFA and expand over several months or years.
Can Zero Trust stop ransomware?
Yes. Zero Trust limits lateral movement, making it harder for ransomware to spread across systems.
Why is Zero Trust better than VPNs?
VPNs grant broad access once connected. Zero Trust enforces verification at every step, reducing insider and external risks.
What are examples of Zero Trust tools?
Examples include Microsoft Entra ID, Okta, CrowdStrike EDR, Palo Alto Cortex XDR, and Splunk analytics.
Can small businesses use Zero Trust?
Yes. Cloud-native IAM and endpoint tools make Zero Trust affordable for SMBs.